HOSHI: USE CASE FACTORY
Discover advanced cyberattacks in a single click
Take your cyber threat detection to the next level by powering Jizô AI with threat intelligence
3X FASTER DETECTION
OF ADVANCED THREATS

- Daily update of use cases for cutting-edge coverage.
- Instantly discover advanced threats and measure their progress in the network
JIZÔ AI + HOSHI:
UNMATCHED CONTEXTUALIZATION CAPABILITIES
- Hoshi combined with Jizô AI makes it possible to detect an attack from the initial phase.
- The USE CASES enrich Jizô AI detection rules database. Operators can then choose to integrate the relevant scenarios, based on their industry and specific risk exposure.
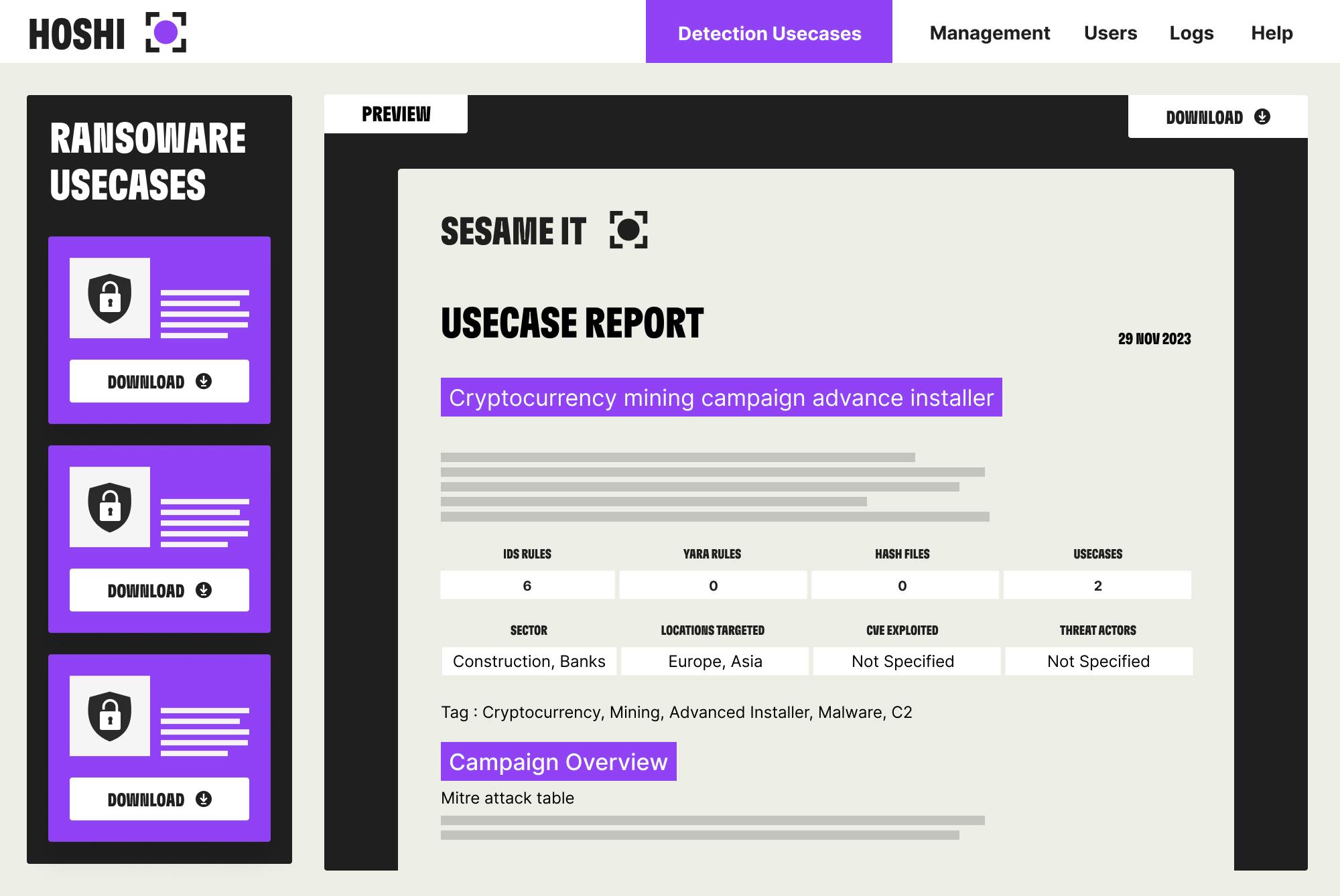
NEW ADVANCED THREAT: ARE WE AFFECTED?
WITH THE USUAL PROCESS:
Requires extensive skills, resources and time to enable the whole process
- Get access to all the latest attack Use Cases
- Instantly detect ongoing attacks by feeding Jizô AI with related Use Cases
LET'S TRY HOSHI
Accelerate your detection of advanced threats with Hoshi
GET A DEMO
