JIZÔ AI: REVEALS ALL THREATS
Operational teams have an efficient solution for implementing a robust cyber defense strategy.
BENEFIT FROM THE MOST
COMPLETE VISIBILITY

CLOUD , HYBRID, ON-PREMISE NETWORKS

IT & OT SYSTEMS
ULTRA ADVANCED CYBER AI
TO DETECT COMPLEX AND UNKNOW THREATS
Jizô AI’s deep learning algorithms continuously learn from your business data and operations.
Get the most comprehensive view and correlation of security incidents accross your entire enterprise.

Preemptive threat detection: identify anomalies and suspicious behavior in real time, even for unknown or evolving attacks. This enables quicker and more anticipatory detection of cyber threats.

Reduction of false positives: thanks to its ability to analyze large amounts of data and learn complex patterns, Jizô AI can more accurately distinguish between a real threat and normal activity, thereby reducing false positives and unnecessary alerts.

Continuous improvement and scalability : our Cyber AI continuously evolve and scale effortlessly, providing ever stronger protection across complex and growing environments
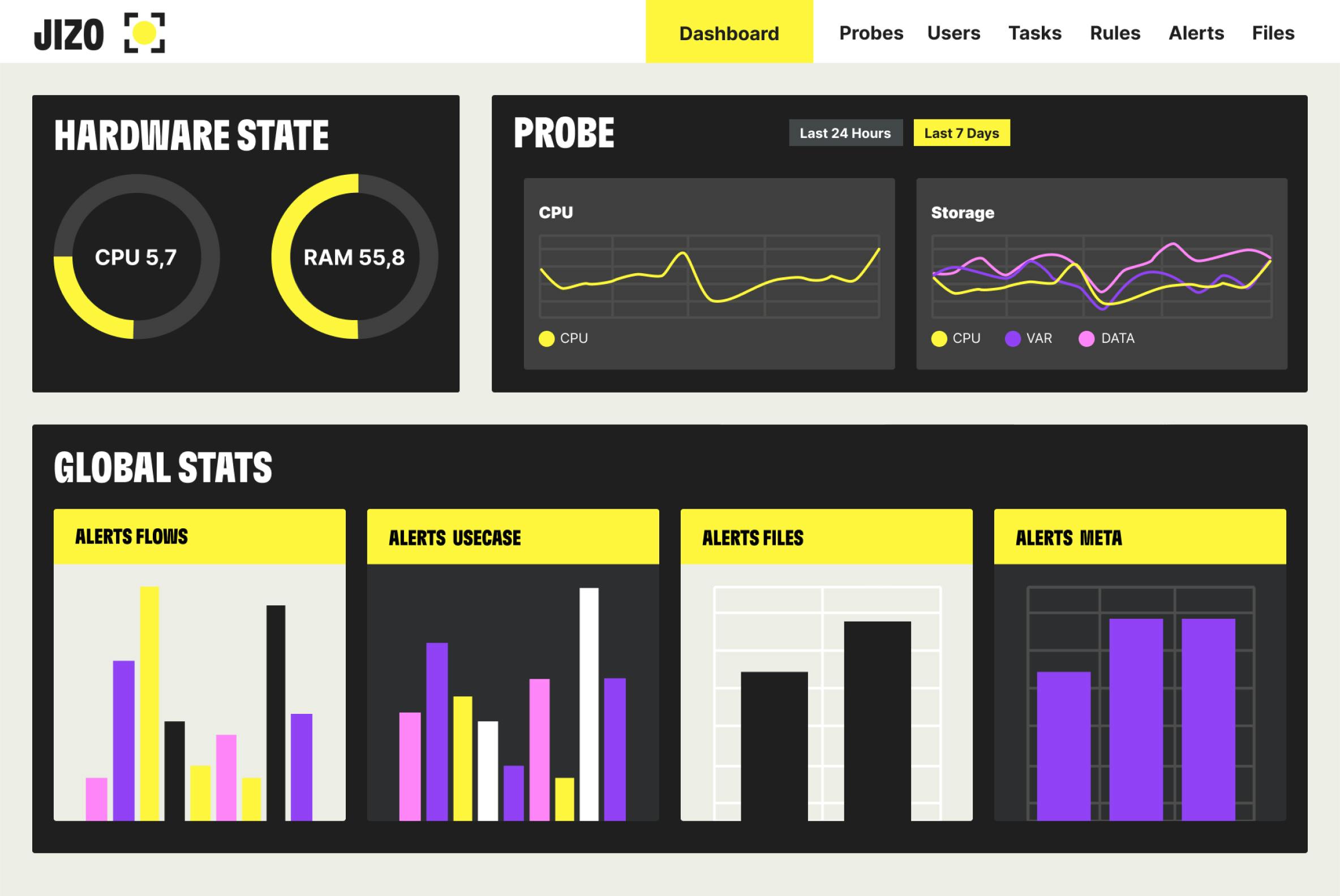
7 SPECIFIC DETECTION ENGINES
FOR THE MOST COMPLETE TRAFFIC ANALYSIS
Jizô AI unique multi-layer technology ensures real-time detection of any threat.


Detection in IT and OT networks

Detection in crypted and unencrypted traffic

You can power Jizô AI with daily fresh CTI detection scenarios in just one click

BENEFIT FROM MORE EXPLAINABILITY
TO REACT FASTER
TRUSTED BY THE MOST DEMANDING ORGANIZATIONS
TO SECURE THEIR CRITICAL NETWORKS

SECURED BY DESIGN

NO DATA SHARING

NO BLACK BOX



CTI TO BEAT ADVANCED THREATS AND COVER YOUR SPECIFIC RISKS

DETECTION SETS FACTORY
3X less time to uncover advanced threats with Hoshi Detection Sets.

WIN PRECIOUS TIME
WHEN INVESTIGATING
ON NEW THREATS


Every day, our CTI experts script and release detection sets for emerging threats that may target your organisation.

Add them to your Jizô AI to instantly discover attacks and measure their progress in your network.

Save your teams valuable time by drastically reducing investigation duration.
FLEXIBLE,
FOR SPECIFIC
DETECTION AND USE
Real-time threat detection in encrypted and unencrypted network traffic
HIGH TRAFFIC PERFORMANCE
- Up to 40 Gbp/s of traffic, and exploitation of thousands of metadata in real time
- Detection even on encrypted traffic
- Full transparency of traffic captured and analyzed, with indication in the event of packet loss